Tracking a Chef with OSINT: From Festival to Phone Digits
Sometimes OSINT challenges are about huge datasets.
Sometimes… it’s just a chef, a profile photo, and a trail of breadcrumbs.
This one was the second type.
Part 1 — Finding the Mystery Gastronomic Event
Goal: Identify which gastronomic festival a hospitality professional attended.
We start with a public professional profile:
👉 https://gronda.com/@konstantin-gladkix
From the profile we extract the basics:
- Name: Константин Гладких (Konstantin Gladkix)
- Username: konstantin-gladkix
- Bio: Sous Chef @ Синара центр
Nothing directly mentions an event. Classic OSINT situation — no explicit data, so we pivot.
Profile Image Recon
The profile photo contains visible text:

The string GA5TREET is visible.
That’s unusual enough to be a strong pivot keyword. A quick search reveals it’s the name of a gastronomic festival.
Event identified.
Flag: OSINT{GA5TREET}
Sometimes the answer really is staring right at you.
Part 2 — Finding the Email Address
Goal: Identify a personal email address using public sources.
Targets rarely exist on one platform only. So we pivot using name + username.
Using a web search module from an OSINT toolkit, I searched for additional profiles.
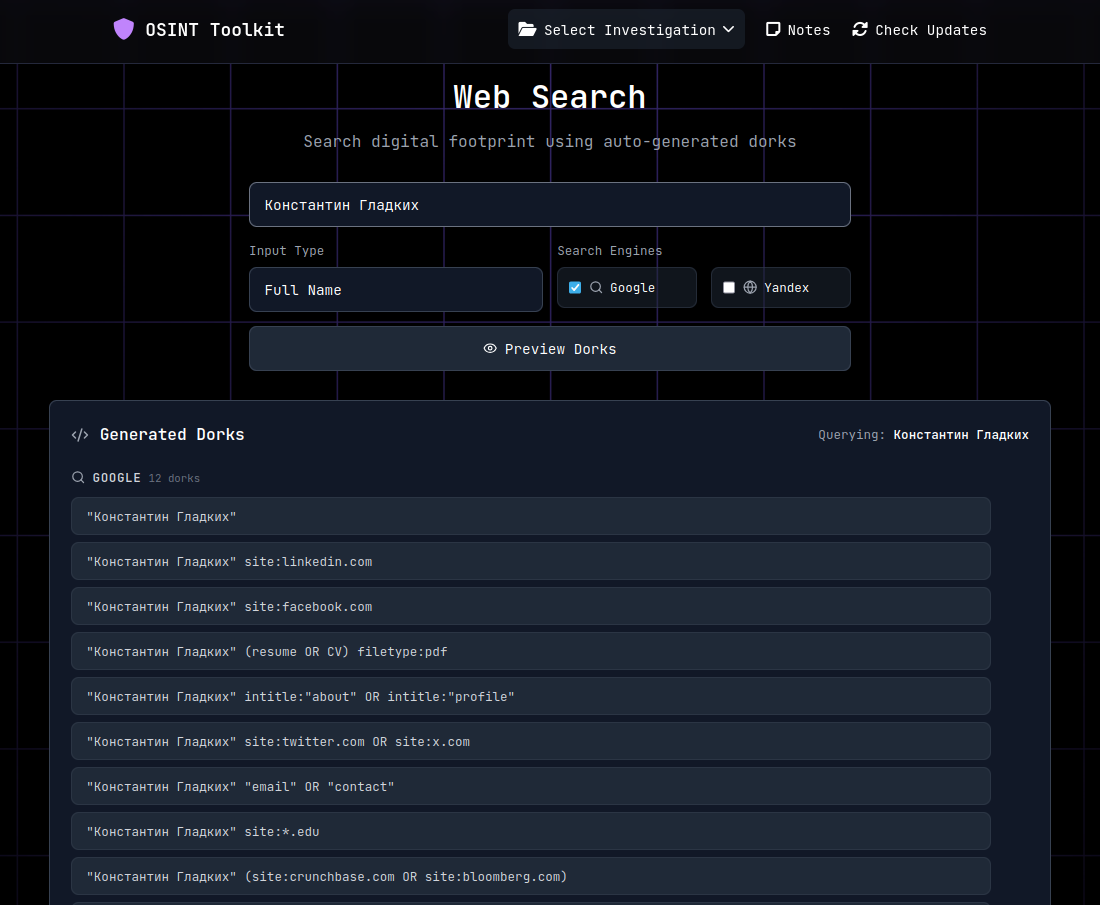
The search reveals multiple platforms:
- VK
Profile overview:
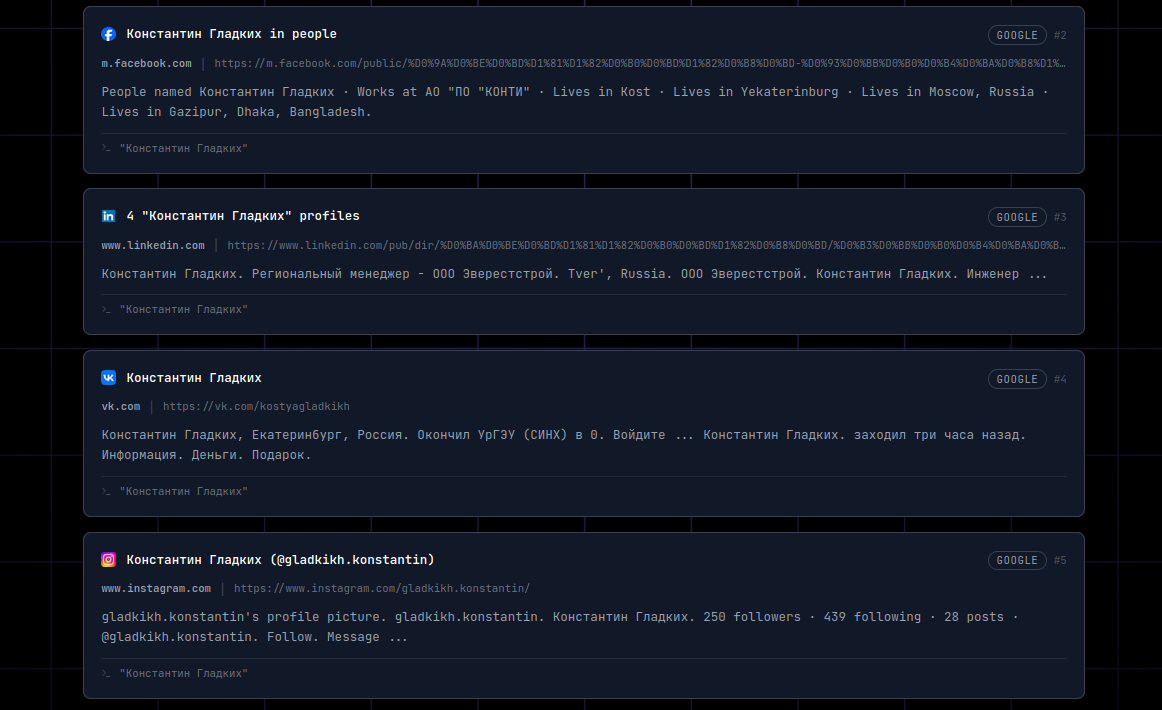
Among these, VK is the most interesting. Older platforms often leak historical data.
Historical Profile Analysis
Using a VK archival bot on telegram, I retrieved historical records of the VK profile.
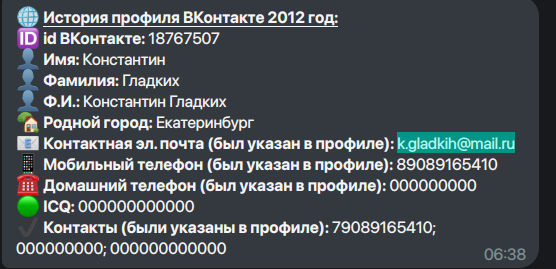
A snapshot from 2012 exposes a public email address:
k.gladkih@mail.ru
Converted to challenge format:
Flag: OSINT{K_DOT_GLADKIH_AT_MAIL_DOT_ru}
Part 3 — Recovering Phone Digits
Goal: Identify the last four digits of the phone number.
If you look closely, the previous VK archive contains more than just an email.
The phone number is visible in the archived data.
Only the last four digits are required.
Extracted digits:
5410
Flag: OSINT{5410}
Tools used in this CTF
1 | Osint-Toolkit (https://github.com/ayxkaddd/Osint-ToolKit) |